Detection CVE-2024-35250
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added a security flaw to its Known Exploited Vulnerabilities (KEV) catalog on December 16th, citing evidence of active exploitation in the wild.
I’ve verified that a Proof of Concept (PoC) is already available, and due to the high-risk nature of this vulnerability, I decided to share this detection.
Update 02/24/2025
The detection rule was added to the sigma repository in Merge PR #5136.
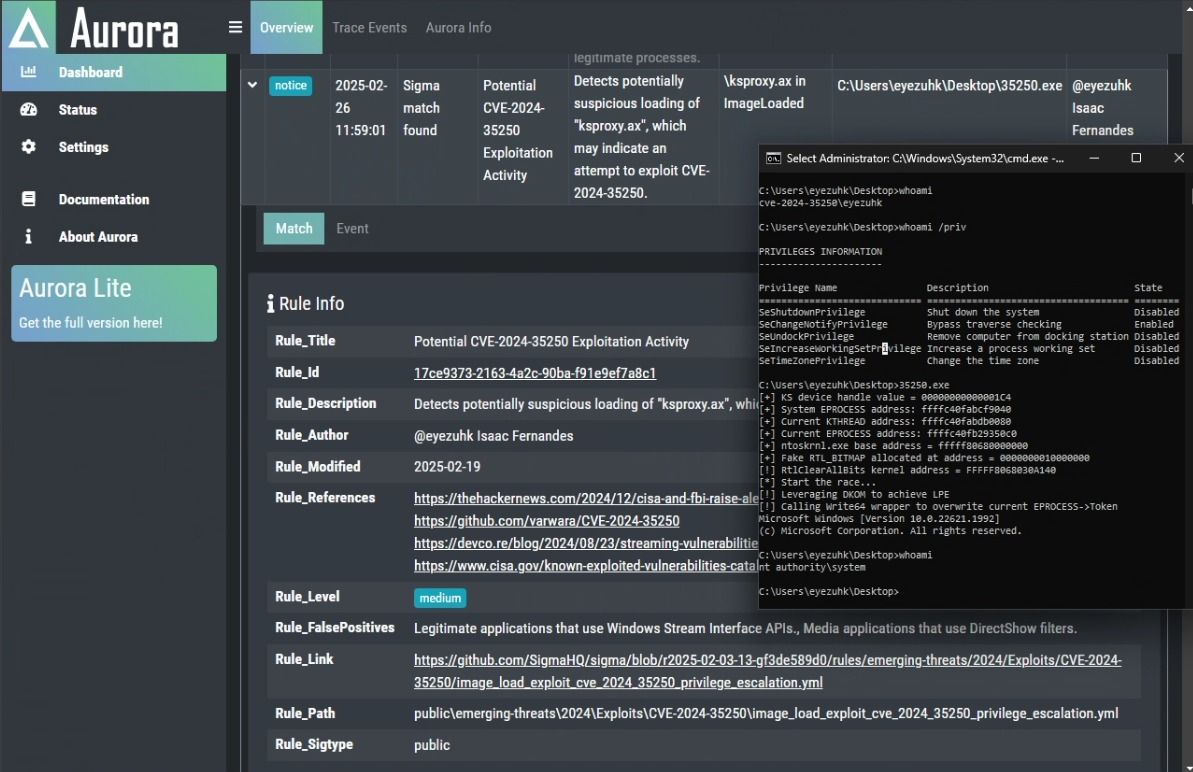
Here is the final version of the updated rule.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
title: Potential CVE-2024-35250 Exploitation Activity
id: 17ce9373-2163-4a2c-90ba-f91e9ef7a8c1
status: experimental
description: |
Detects potentially suspicious loading of "ksproxy.ax", which may indicate an attempt to exploit CVE-2024-35250.
references:
- https://thehackernews.com/2024/12/cisa-and-fbi-raise-alerts-on-exploited.html
- https://github.com/varwara/CVE-2024-35250
- https://devco.re/blog/2024/08/23/streaming-vulnerabilities-from-windows-kernel-proxying-to-kernel-part1-en/
- https://www.cisa.gov/known-exploited-vulnerabilities-catalog
author: '@eyezuhk Isaac Fernandes'
date: 2025-02-19
tags:
- attack.privilege-escalation
- attack.t1068
- cve.2024-35250
- detection.emerging-threats
logsource:
category: image_load
product: windows
detection:
selection:
ImageLoaded|endswith: '\ksproxy.ax'
filter_main_system_paths:
Image|startswith:
- 'C:\Program Files\'
- 'C:\Program Files (x86)\'
- 'C:\Windows\System32\'
- 'C:\Windows\SysWOW64\'
filter_optional_teams:
Image|endswith: '\AppData\Local\Microsoft\Teams\current\Teams.exe'
filter_optional_zoom:
Image|endswith: '\AppData\Roaming\Zoom\bin\Zoom.exe'
filter_optional_firefox:
Image|endswith: '\AppData\Local\Mozilla Firefox\firefox.exe'
filter_optional_chrome:
Image|endswith: '\AppData\Local\Google\Chrome\Application\chrome.exe'
filter_optional_opera:
Image|endswith: '\AppData\Local\Programs\Opera\opera.exe'
filter_optional_discord:
Image|endswith: '\AppData\Local\Discord\app-*\Discord.exe'
condition: selection and not 1 of filter_main_* and not 1 of filter_optional_*
falsepositives:
- Legitimate applications that use Windows Stream Interface APIs.
- Media applications that use DirectShow filters.
level: medium
Old detection
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
title: Privilege Escalation via CVE-2024-35250
id: 17ce9373e-2163-4a2c-90ba-f91e9ef7a8c1
status: experimental
description: Detects when cmd.exe with system privileges is executed after a process loads 'ksproxy.ax' and 'ksuser.dll', indicating potential exploitation of CVE-2024-35250.
references:
- https://thehackernews.com/2024/12/cisa-and-fbi-raise-alerts-on-exploited.html
- https://github.com/varwara/CVE-2024-35250
- https://devco.re/blog/2024/08/23/streaming-vulnerabilities-from-windows-kernel-proxying-to-kernel-part1-en/
- https://www.cisa.gov/known-exploited-vulnerabilities-catalog
author: '@eyezuhk Isaac Fernandes '
date: 2024-12-19
tags:
- attack.t1068
- attack.exploitation_for_privilege_escalation
- cve.2024.35250
logsource:
product: windows
service: sysmon
category: process
definition: 'Sysmon event logs capturing process image loads and registry modifications'
eventid:
- 7 # Image Loaded
- 13 # Registry event
detection:
selection_imgload:
EventID: 7
ImageLoaded|endswith:
- "ksproxy.ax"
- "ksuser.dll"
User: not "NT AUTHORITY\\SYSTEM"
selection_registry:
EventID: 13
TargetObject|contains: "HKLM\\System\\CurrentControlSet\\Services\\bam\\State\\UserSettings\\S-1-5-18\\Device\\HarddiskVolume*\\Windows\\System32\\cmd.exe"
User: "NT AUTHORITY\\SYSTEM"
condition: selection_imgload and selection_registry
falsepositives:
- Legitimate system processes that load ksproxy.ax and ksuser.dll may trigger this rule.
level: high
Exploration demo video.
Example Log Event
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
Event 7
Image loaded:
RuleName: -
UtcTime: 2024-12-19 23:56:09.689
ProcessGuid: {cc3062fa-b299-6764-cd01-000000000500}
ProcessId: 4220
Image: C:\Users\eyezuhk\Desktop\CVE-2024-35250.exe
ImageLoaded: C:\Windows\System32\ksproxy.ax
FileVersion: 10.0.22621.1 (WinBuild.160101.0800)
Description: WDM Streaming ActiveMovie Proxy
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: ksproxy.ax
Hashes: SHA1=46B1CC076C1AE967416E9EA18E5B95A48493B029,MD5=EC540CDBEBC7584F562944CD28C115FB,SHA256=598A3C648DE2B983CFDB2AC599B1254D77FEC868282083E03D65FDCF24847719,IMPHASH=BC80C0BAA52122435D413CD1EAC2C285
Signed: true
Signature: Microsoft Windows
SignatureStatus: Valid
User: ISAACFN\eyezuhk
Image loaded:
RuleName: -
UtcTime: 2024-12-19 23:56:09.718
ProcessGuid: {cc3062fa-b299-6764-cd01-000000000500}
ProcessId: 4220
Image: C:\Users\eyezuhk\Desktop\CVE-2024-35250.exe
ImageLoaded: C:\Windows\System32\ksuser.dll
FileVersion: 10.0.22621.1 (WinBuild.160101.0800)
Description: User CSA Library
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: ksuser.dll
Hashes: SHA1=EF8A8E9BB22E736095904876A8F1BB776BB72063,MD5=46B06DAB488A1E7339898EC4A9AC66C8,SHA256=3F28C73A70527247E64479197C93EF6732EEF6021860037163C7C479AD3CF2FB,IMPHASH=B1B9119A4C6D367DD41A0820244C09EB
Signed: true
Signature: Microsoft Windows
SignatureStatus: Valid
User: ISAACFN\eyezuhk
Event 13
Registry value set:
RuleName: -
EventType: SetValue
UtcTime: 2024-12-19 23:56:09.808
ProcessGuid: {cc3062fa-b299-6764-cd01-000000000500}
ProcessId: 4220
Image: C:\Users\eyezuhk\Desktop\CVE-2024-35250.exe
TargetObject: HKLM\System\CurrentControlSet\Services\bam\State\UserSettings\S-1-5-18\Device\HarddiskVolume4\Windows\System32\cmd.exe
Details: Binary Data
User: NT AUTHORITY\SYSTEM
Enjoy Reading This Article?
Here are some more articles you might like to read next: